Images related to complexity science I found useful in putting together a presentation dealing with Strategic Foresight and Warning and Complexity
2213 – 2218 EVT – A Current Account Surplus? Think again! (Mamominarch)
Last weeks’ summary: In 2212 EVT, Everstate (the ideal-type corresponding to our very real countries created to foresee the future of governance and of the modern nation-state) knows a rising dissatisfaction of its population. To face the various difficulties and widespread discontent, in a first scenario, Everstate’s governing bodies have transformed the conclusions of the Mamominarch Commission into policies. They have thus started implementing the programme of drastic reduction of public expenses through privatization and outsourcing, transfer of responsibilities to local administrations and increased reliance on The Regional Union, accompanied by a temporary increase in income and consumption taxes. The first months of reforms have been successful and the situation appears to improve. (The reader can click on each picture to see a larger version in a new tab – a navigating map of posts is …
Continue reading “2213 – 2218 EVT – A Current Account Surplus? Think again! (Mamominarch)”
Featured Images, Symbols & Foresight Product: the Example of The Chronicles of Everstate
(updated 17 April 2012) When an image is featured and is meant to represent the totality of a foresight or anticipatory product, or a large section of it, it must capture the gist of the product. Symbols and symbolism are then crucial to transmit messages. This importance of symbols should anyway be considered for any use of image (as well as when developing a scenario narrative, for example when choosing names). This will be exemplified here with the Chronicles of Everstate. The image aims at capturing symbolically the features of the contemporary (early 21st century) modern nation-state: It, of course, is an heir to Hobbes Leviathan. However, compared with the original image, the head of the sovereign is not displayed …
Visual Tools and Design for Foresight Products
Delivery to clients of strategic foresight and warning (SF&W) or futures related products is, as we saw, a crucial part of the overall SF&W process. Without delivery, there is neither warning nor foresight, however accurate and brilliant the underlying analyses. As crucial, although very difficult to achieve, is the fact that clients or customers must pay heed to the foresight product or to the warning. Initially, according to the intelligence literature, notably on surprise, or to exchanges with practitioners, this part of the process is seen as so difficult indeed that it is not considered as being the responsibility of the foresight and warning – or risk – analyst, officer or of the scientist if we include science in SF&W, given the predictive …
Continue reading “Visual Tools and Design for Foresight Products”
2212-2213 EVT – Implementing the Mamominarch conclusions
Last weeks’ summary: In 2012 EVT, Everstate (the ideal-type corresponding to our very real countries created to foresee the future of governance and of the modern nation-state) knows a rising dissatisfaction of its population. To face the various difficulties and widespread discontent, Everstate’s governing authorities decide to follow the conclusions of the Mamominarch Commission that recommend to drastically reduce state expenditures. (The reader can click on each picture to see a larger version in a new tab – a navigating map of posts is available to ease reading – methodological or research note at the bottom of the post). The Mamominarch conclusions become policy All governing bodies thus adopt the conclusions of the Mamominarch Commission. New laws are enacted when needed, which is easily done as the major parties seating in …
Continue reading “2212-2213 EVT – Implementing the Mamominarch conclusions”
Anonymous: a new political force?
Anonymous: a new political force?
 Anonymous, the Anonymous movement, idea or “Internet meme,” to use Wikipedia characterisation, has become an increasingly important actor on the global political scene, which cannot be ignored anymore.
Anonymous, the Anonymous movement, idea or “Internet meme,” to use Wikipedia characterisation, has become an increasingly important actor on the global political scene, which cannot be ignored anymore.
It is, however, rarely seen as a political actor, despite Anonymous’ evolution, as Al Jazeera’s excellent timeline makes quite clear, as Quinn Norton for Wired details with her very interesting three-part series examining the history of Anonymous, or as shown on the video A Short, Strange History of Anonymous posted by Ryan Singel for Wired.
It is rather usually labelled as a group composed of hacktivists (most media), hackers and IT criminals (e.g. Interpol), even recently as hackers who “could have the ability within the next year or two to bring about a limited power outage through a cyber attack” in the US, as reported by The Wall Street Journal, citing comments by the Director of the National Security Agency U.S. Cyber Command Gen. Keith Alexander, done “in private meetings at the White House and elsewhere“(CNET).
 On the contrary, for Anonymous participants (Anons), Anonymous is indeed “an idea,” (AP citing twitter) “the will of the people” (CNET interview). Accordingly, Anonymous creates strong reactions on a large spectrum ranging from sympathy and admiration to fear and dislike according to a recent ongoing internet polls done by SodaHeadNews.
On the contrary, for Anonymous participants (Anons), Anonymous is indeed “an idea,” (AP citing twitter) “the will of the people” (CNET interview). Accordingly, Anonymous creates strong reactions on a large spectrum ranging from sympathy and admiration to fear and dislike according to a recent ongoing internet polls done by SodaHeadNews.
As time allows, I shall try to follow and document here, the evolution of Anonymous as a political actor, from a political science point of view.
———-
References
Gorman, Siobhan “Alert on Hacker Power Play: U.S. Official Signals Growing Concern Over Anonymous Group’s Capabilities,” The Wall Street Journal, February 21, 2012. Accessed 5 March 2012.
Haddad, Mohammed, “Interactive timeline: Anonymous – A history of the global cyberactivist movement, from “lulz” to revolutions,” Al Jazeera, Last Modified: 19 May 2011. Accessed 5 March 2012.
Interpol, Media release, “Hackers reportedly linked to ‘Anonymous’ group targeted in global operation supported by INTERPOL,” 28 February 2012. Accessed 5 March 2012.
Keller, Greg “Interpol says suspected Anonymous hackers arrested,” Associated Press, 29 February 2012. Accessed 5 March 2012.
Mills, Elinor, “How Anonymous channels ‘the will of the people – Q&A,” February 28, 2012, CNET. Accessed 5 March 2012.
Norton, Quinn, three-part series examining the history of Anonymous, December 2011 -January 2012, Wired. Accessed 5 March 2012.
Reisinger, Don, “Scared of Anonymous? NSA chief says you should be,” CNET, February 21, 2012. Accessed 5 March 2012.
Singel, Ryan, A Short, Strange History of Anonymous (video), January 6, 2012, Wired. Accessed 5 March 2012.
SodaHead News Polls, “Police Arrest 25 ‘Anonymous’ Hackers: Is Anonymous Admirable or Adverse?” started February 29, 2012, SodaHead News. 1,034 votes and 1,198 opinions on March 5, 2012. Accessed 5 March 2012.
Wikipedia, “Anonymous (group).” Accessed 5 March 2012.
2212 EVT – Scenario 1 – Mamominarch: Off with the State
Last weeks’ summary: In 2012 EVT, Everstate (the ideal-type corresponding to our very real countries created to foresee the future of governance and of the modern nation-state) knows a rising dissatisfaction of its population. Plagued with a deepening budget deficit and an increasing need for liquidity, a related creeping appropriation of resources while the strength of central public power weakens to the profit of various elite groups and with an outdated worldview that promotes misunderstanding, disconnect and thus inadequate actions, the political authorities are increasingly unable to deliver the security citizens seek and risks to the legitimacy of the whole system increases. Alarmed by the rising difficulties and widespread discontent, the governing authorities decide to do something. Three potential scenarios or stories will be told: “Mamominarch: Off with the State,” “Panglossy: Same Old, Same Old,” and …
Continue reading “2212 EVT – Scenario 1 – Mamominarch: Off with the State”
2212 EVT: Material Stakes in an Outdated Worldview (The Chronicles of Everstate)
Last week’s summary: In 2212 EVT, Everstate (the ideal-type corresponding to our very real countries created to foresee the future of the modern nation-state) knows a rising dissatisfaction of its population as authorities cannot anymore deliver security. The last phenomenon driving Everstatan governing bodies’ rising inefficiency in ensuring their mission is an outdated worldview that leads to misunderstanding and disconnect, which is first upheld by ideological stakes. (The reader can click on each picture to see a larger version in a new tab – back to the Table of contents). The knowledge institutions and related people, which are guardians of norms and thus have ideological stakes in upholding an outdated worldview, are also motivated by material stakes in seeing norms respected, upheld and continuing. Indeed, their institutional survival depends on the continuation of …
Continue reading “2212 EVT: Material Stakes in an Outdated Worldview (The Chronicles of Everstate)”
Russia 2045
Russia 2045 – Strategic Social Movement
Russia 2045 is an interesting Russian initiative for the future. It wants to be more than that, a movement for a new paradigm, indeed a new ideology according to its Manifesto, organised around the creation of “working cybernetic organisms,” with Russia as leader. It is close to the Singularity idea, and, indeed, Ray Kurzweil featured as speaker during the Global Future 2045 congress held in Moscow from 16 to 20 February 2012.* The reasons for and objective of the Movement are well explained in the video (below) created for GF2045. The websites of both Russia 2045 and GF 2045 hold a host of very interesting articles and videos.
Russia 2045 was initially created on February 2011 by Dmitri Itskov, President of New Media Stars (also Domestic Limited-Liability Company incorporated in Las Vegas, Nevada), and includes Russian scientists in its initiative group. As an aside, it is also supported by an American actor Steven Seagal, who asked Putin to support the movement in May 2011.
According to the website, GF 2045 was supported by the Eurasian Center for Big History & System Forecasting, the Institute of Oriental Studies and the Russian Academy of Sciences. The Eurasian Center for Big History & System Forecasting was founded on May 25, 2011 by the Academic Council of The Institute of Oriental Studies of the Russian Academy of Sciences (RAS). Its mission statement reads as follows: “The Eurasian Center for Big History & System Forecasting (ECBSF) seeks to develop a unified and interdisciplinary history of the Cosmos, Earth, Life and Humanity. It also seeks to develop system forecasting of social, political, demographic, ethnic and cultural processes at regional and global levels.” Among its tasks, one finds “political consulting,” which positions the Center firmly into the current scientific evolution, and shows a global effort endeavoured by science to take back its place as policy-making advisor, as also exemplified, in a different way, by the LSE-led Impact of Social Science Project.
The next GF2045 congress should be held during Spring 2013, in New York City.
* Ricardo K. Sulzbachwas @rkucerasulzbach initially mentionned GF2045 on Twitter.
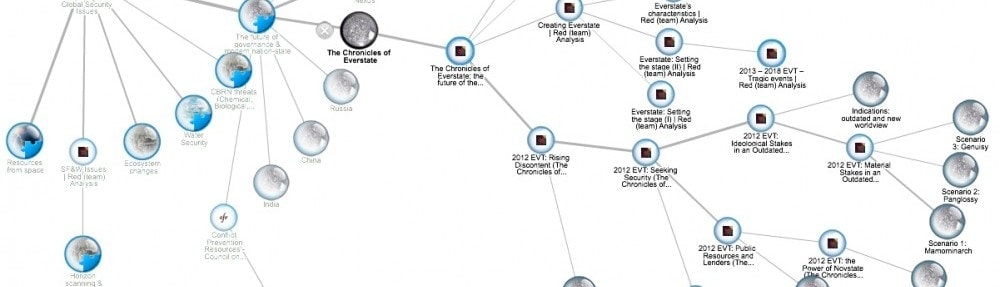
Navigating the Chronicles of Everstate
The featured image for this post is a snapshot of a map done with Pearltrees. This page is about presenting ways to follow and access the series of posts constituting The Chronicles of Everstate, beyond the usual linear menus or the detailed outline in the website footer. This idea, mapping the very posts of The Chronicles of Everstate, is a direct result of the interactive quality of this foresight experiment. One faithful reader, indeed, underlined that, as the number of posts increased, reading and understanding was becoming more complex, notably for newcomers. He suggested that a map would be very helpful to allow users and readers to navigate among posts. We then discussed various ways to implement this idea. Here are …
Continue reading “Navigating the Chronicles of Everstate”